Q-Day
For quantum computing and post-quantum realted answers, you can use the AI tool that answers questions using a curated corpus of information from PostQuantum.com, NIST, NSA, and ENISA and other reliable sources. Ask anything related to quantum computing or quantum security. Or just check out below the selection of Q-Day related articles from PostQuantum.com.
-

PQC ROI the Honest Way
Many organizations are hesitating to invest in post-quantum cryptography (PQC) because the return on investment (ROI) is not immediately obvious.…
Read More » -

Post-Quantum Negligence: Legal Risks of Failing to Prepare for the Quantum Threat
Quantum computing is no longer a far-off hypothesis - it’s a rapidly emerging reality that could render today’s encryption obsolete.…
Read More » -
Trust Now, Forge Later (TNFL) – The Overlooked Quantum Threat
What is "Trust Now, Forge Later" (TNFL)? Most discussions about quantum computing threats focus on “Harvest Now, Decrypt Later” (HNDL)…
Read More » -
Forget Q-Day Predictions – Regulators, Insurers, Investors, Clients Are Your New Quantum Clock
Whether you personally believe Q-Day will come in 5 years or 50, the world around you isn’t taking chances -…
Read More » -
CRQC Readiness Benchmark vs. Quantum Threat Tracker (QTT)
I will try and compare my proposed CRQC Readiness Benchmark with QTT, highlighting fundamental differences in methodology, assumptions, and philosophy,…
Read More » -
How You, Too, Can Predict Q-Day (Without the Hype)
For three decades, Q-Day has been “just a few years away.” I want to show you how to make your…
Read More » -
The Trouble with Quantum Computing and Q-Day Predictions
The trouble with quantum computing predictions so far has been that too many have been more speculation than science, more…
Read More » -
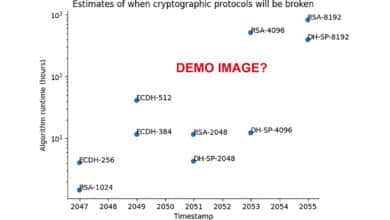
Quantum Threat Tracker (QTT) Review Praising the Tool Questioning the Demo
The Quantum Threat Tracker (QTT) is a newly released open-source tool by Cambridge Consultants and the University of Edinburgh that…
Read More » -
What is the Quantum Threat? A Guide for C‑Suite Executives and Boards
Boards do not need to dive into the scientific intricacies of qubits and algorithms, but they do need to recognize…
Read More » -
CRQC Readiness Benchmark – Benchmarking Quantum Computers on the Path to Breaking RSA-2048
Benchmarking quantum capabilities for cryptography is both critical and challenging. We can’t rely on any single metric like qubit count…
Read More » -
Q-Day Revisited – RSA-2048 Broken by 2030: Detailed Analysis
It’s time to mark a controversial date on the calendar: 2030 is the year RSA-2048 will be broken by a…
Read More » -
What Is Q-Day (Y2Q)?
Q-Day, sometimes called “Y2Q” or the “Quantum Apocalypse”, refers to the future moment when a quantum computer becomes powerful enough…
Read More » -
The Enormous Energy Cost of Breaking RSA‑2048 with Quantum Computers
The energy requirements for breaking RSA-2048 with a quantum computer underscore how different the post-quantum threat is from conventional hacking.…
Read More » -
Breaking RSA Encryption: Quantum Hype Meets Reality (2022–2025)
To put it plainly, if you encrypted a message with an RSA-2048 public key today, no one on Earth knows…
Read More » -
Post-Quantum Cryptography (PQC) Standardization – 2025 Update
Post-quantum cryptography (PQC) is here - not in theory, but in practice. We have concrete algorithms, with standards guiding their…
Read More »