These resources give you the tools to understand quantum computing progress and estimate when cryptographically relevant quantum computers (CRQCs) will arrive.
How the Methodology Works
The prediction framework has three layers that build on each other: Eight Capabilities → Three Levers → One Benchmark Score → Timeline Prediction
1. The full methodology The CRQC Quantum Capability Framework identifies ten fundamental capabilities needed to break RSA-2048 encryption
2. These combine into three key levers that capture what matters most:
– LQC (Logical Qubit Capacity): How many error-corrected qubits are available
– LOB (Logical Operations Budget): How many quantum gates can run reliably in sequence
– QOT (Quantum Operations Throughput): How many operations per second the system achieves
3. The CRQC Readiness Benchmark – Benchmarking Quantum Computers on the Path to Breaking RSA-2048 explains these three levers and combines them into a single score showing current progress toward RSA-2048 breaking capability (currently ~0.05%). Simplified how-to How You, Too, Can Predict Q-Day (Without the Hype) shows you how to use those three levers.
4. The CRQC Readiness Benchmark (Q-Day Estimator) Tool helps you tweak your own parameters and assumptions to come up with your own current capability scope (the CRQC Benchmark). It then takes that current capability score plus an annual growth factor to project when we’ll reach 100% (Q-Day)
5. The Quantum Computing Roadmaps track all main quantum hardware companies, assessing them on track record – have they consistently hit past milestones? This separates credible roadmaps from marketing hype, helping you weight vendor predictions appropriately. It gives you a reality check: who’s actually delivering and how close to your prediction are their roadmaps?
How They Work Together? Learn the framework → See where we are today → Project your own timeline → Validate against real progress
Why This Matters to You
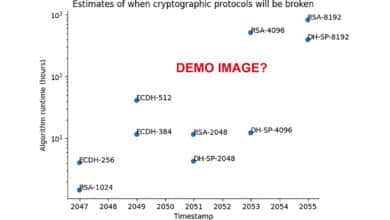
The current consensus points to 2030 ±2 years for CRQC capability. But rather than trusting any single prediction (including mine), these resources empower you to:
– Evaluate vendor announcements critically
– Adjust timelines as technology advances
– Make informed decisions about post-quantum cryptography migration
– Explain quantum threats to leadership with data-backed reasoning
Your organization’s cryptographic migration timeline is 5-10+ years. Understanding when quantum computers become cryptographically relevant isn’t just academic – it helps you with the risk exposure prediction.